Windows clients. Download and install the OpenVPN client (version 2.4 or higher) from the official OpenVPN website. Download the VPN client profile package from the Azure portal, or use the 'New-AzVpnClientConfiguration' cmdlet in PowerShell. Unzip the profile. Next, open the vpnconfig.ovpn configuration file from the OpenVPN folder using Notepad. OpenVPN enables you to create an SSL-based VPN (virtual private network) that supports both site-to-site and client-to-site tunnels. This allows your road warrior users to connect to local resources as if they were in the office, or connect the networks of several geographically distant offices together - all with the added security of encryption protecting your data. OpenVPN Connect OpenVPN Connect is our official client. Use OpenVPN Connect to connect to OpenVPN Cloud, Access Server or any OpenVPN compatible server/service. Select your platform and download here. Recently Windows 10 got updated. After update, the VPN has stopped getting connected. Tried other VPN services but it isnt working. Also deleted and reloaded the VPN app. Nothing seems to be working.
-->This article helps you configure OpenVPN ® Protocol clients. You can also use the Azure VPN Client for Windows 10 to connect via OpenVPN protocol. For more information, see Configure a VPN client for P2S OpenVPN connections.
Before you begin
Create a User VPN (point-to-site) configuration. Make sure that you select 'OpenVPN' for tunnel type. For steps, see Create a P2S configuration for Azure Virtual WAN.
Windows clients
Download and install the OpenVPN client (version 2.4 or higher) from the official OpenVPN website.
Download the VPN client profile package from the Azure portal, or use the 'New-AzVpnClientConfiguration' cmdlet in PowerShell.
Unzip the profile. Next, open the vpnconfig.ovpn configuration file from the OpenVPN folder using Notepad.
Export the point-to-site client certificate you created and uploaded. Use the following article links:
VPN Gateway instructions
Virtual WAN instructions
Extract the private key and the base64 thumbprint from the .pfx. There are multiple ways to do this. Using OpenSSL on your machine is one way. The profileinfo.txt file contains the private key and the thumbprint for the CA and the Client certificate. Be sure to use the thumbprint of the client certificate.
Open profileinfo.txt in Notepad. To get the thumbprint of the client (child) certificate, select the text (including and between)'-----BEGIN CERTIFICATE-----' and '-----END CERTIFICATE-----' for the child certificate and copy it. You can identify the child certificate by looking at the subject=/ line.
Switch to the vpnconfig.ovpn file you opened in Notepad from step 3. Find the section shown below and replace everything between 'cert' and '/cert'.
Open the profileinfo.txt in Notepad. To get the private key, select the text (including and between) '-----BEGIN PRIVATE KEY-----' and '-----END PRIVATE KEY-----' and copy it.
Go back to the vpnconfig.ovpn file in Notepad and find this section. Paste the private key replacing everything between and 'key' and '/key'.
Do not change any other fields. Use the filled in configuration in client input to connect to the VPN.
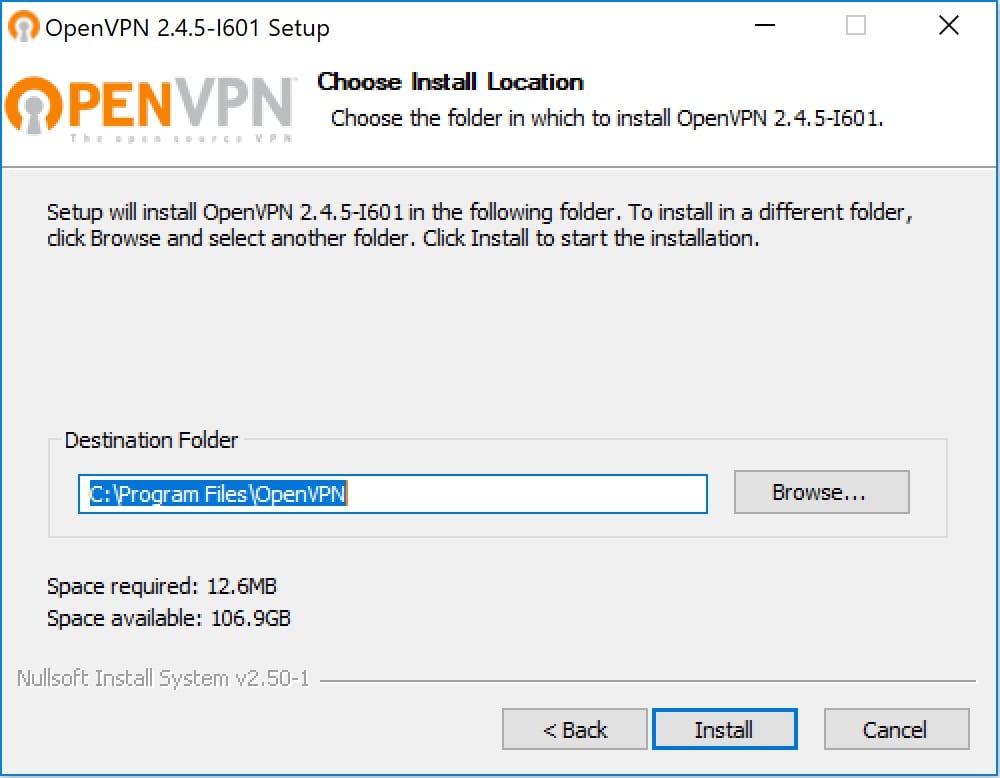
Copy the vpnconfig.ovpn file to C:Program FilesOpenVPNconfig folder.
Right-click the OpenVPN icon in the system tray and click connect.
Mac clients
Download and install an OpenVPN client, such as TunnelBlick.
Download the VPN client profile package from the Azure portal, or use the 'New-AzVpnClientConfiguration' cmdlet in PowerShell.
Unzip the profile. Open the vpnconfig.ovpn configuration file from the OpenVPN folder in a text editor.
Fill in the P2S client certificate section with the P2S client certificate public key in base64. In a PEM formatted certificate, you can open the .cer file and copy over the base64 key between the certificate headers. Use the following article links for information about how to export a certificate to get the encoded public key:
VPN Gateway instructions
Virtual WAN instructions
Fill in the private key section with the P2S client certificate private key in base64. See the Export your private key on the OpenVPN site for information about how to extract a private key.
Do not change any other fields. Use the filled in configuration in client input to connect to the VPN.
Double-click the profile file to create the profile in Tunnelblick.
Launch Tunnelblick from the applications folder.
Click on the Tunnelblick icon in the system tray and pick connect.
Important
Only iOS 11.0 and above and MacOS 10.13 and above are supported with OpenVPN protocol.
iOS clients
Install the OpenVPN client (version 2.4 or higher) from the App store.
Download the VPN client profile package from the Azure portal, or use the 'New-AzVpnClientConfiguration' cmdlet in PowerShell.
Unzip the profile. Open the vpnconfig.ovpn configuration file from the OpenVPN folder in a text editor.
Fill in the P2S client certificate section with the P2S client certificate public key in base64. In a PEM formatted certificate, you can open the .cer file and copy over the base64 key between the certificate headers. Use the following article links for information about how to export a certificate to get the encoded public key:
VPN Gateway instructions
Virtual WAN instructions
Fill in the private key section with the P2S client certificate private key in base64. See Export your private key on the OpenVPN site for information about how to extract a private key.
Do not change any other fields.
E-mail the profile file (.ovpn) to your email account that is configured in the mail app on your iPhone.
Open the e-mail in the mail app on the iPhone, and tap the attached file
Tap on More if you do not see Copy to OpenVPN option
Tap on Copy to OpenVPN
Tap on ADD in the Import Profile page
Tap on ADD in the Imported Profile page
Launch the OpenVPN app and slide the switch in the Profile page right to connect
Linux clients
Open a new Terminal session. You can open a new session by pressing 'Ctrl + Alt + t' at the same time.
Enter the following command to install needed components:
Download the VPN profile for the gateway. This can be done from the Point-to-site configuration tab in the Azure portal.
Export the P2S client certificate you created and uploaded to your P2S configuration on the gateway. Use the following article links:
VPN Gateway instructions
Virtual WAN instructions
Extract the private key and the base64 thumbprint from the .pfx. There are multiple ways to do this. Using OpenSSL on your computer is one way.
The profileinfo.txt file will contain the private key and the thumbprint for the CA, and the Client certificate. Be sure to use the thumbprint of the client certificate.
Open profileinfo.txt in a text editor. To get the thumbprint of the client (child) certificate, select the text including and between '-----BEGIN CERTIFICATE-----' and '-----END CERTIFICATE-----' for the child certificate and copy it. You can identify the child certificate by looking at the subject=/ line.
Open the vpnconfig.ovpn file and find the section shown below. Replace everything between the and 'cert' and '/cert'.
Open the profileinfo.txt in a text editor. To get the private key, select the text including and between '-----BEGIN PRIVATE KEY-----' and '-----END PRIVATE KEY-----' and copy it.
Open the vpnconfig.ovpn file in a text editor and find this section. Paste the private key replacing everything between and 'key' and '/key'.
Do not change any other fields. Use the filled in configuration in client input to connect to the VPN.
To connect using the command line, type the following command:
To connect using the GUI, go to system settings.
Click + to add a new VPN connection.
Under Add VPN, pick Import from file…
Browse to the profile file and double-click or pick Open.
Click Add on the Add VPN window.
You can connect by turning the VPN ON on the Network Settings page, or under the network icon in the system tray.
Next steps
For more information about User VPN (point-to-site), see Create User VPN connections.
'OpenVPN' is a trademark of OpenVPN Inc.
| OpenVPN |
|

- 2Settings
- 2.1Status
- 2.2Server
- 2.3Client
- 2.4Advanced
- 2.4.2Server Configuration and Client Configuration
- 3Reports
- 5OpenVPN FAQs
- 5.1What operating systems are supported?
- 5.2Can I use it with my phone or tablet?
About OpenVPN
OpenVPN enables you to create an SSL-based VPN (virtual private network) that supports both site-to-site and client-to-site tunnels. This allows your road warrior users to connect to local resources as if they were in the office, or connect the networks of several geographically distant offices together - all with the added security of encryption protecting your data. OpenVPN supports any operating system with an OpenVPN-compatible VPN client (which is almost every OS), even smartphones!
The OpenVPN application can run as a server allowing for remote client to connect to the Untangle server, and the OpenVPN application can connect to other remote Untangle servers as a client.
The VPN Overview article provides some general guidance of which VPN technology may be the best fit for different scenarios.
Settings
This section reviews the different settings and configuration options available for OpenVPN.
Status
The Status tab shows you a list of open connections, the time the tunnels were created and transmit statistics.
Connected Remote Clients
This grid shows the currently connected remote clients that are connected to this OpenVPN (if server is enabled.)
| Name | Description |
|---|---|
| Address | The IP of the remote client. |
| Client | The OpenVPN client name. |
| Start Time | The time that the client connected. |
| Rx Data | The amount of data received from this client in this session. |
| Tx Data | The amount of data sent to this client in this session. |
Remote Server Status
This grid shows the remote servers this OpenVPN is connecting to as a client.
| Name | Description |
|---|---|
| Name | The name of the remote server. |
| Connected | The current connection status |
| Rx Data | The amount of data received from this client in this session. |
| Tx Data | The amount of data sent to this client in this session. |
Server
The Server tab includes all the configuration for OpenVPN's server functionality.
Site Name is the name of the this OpenVPN site. A random name is chosen so that it is unique. A new name can be given, but it should be unique across all Untangle sites in the organization. For example, if the company name is 'MyCompany' then 'mycompany' is a bad site name if you have multiple Untangles deployed as it might be used elsewhere. The Site Namemust be unique.
Site URL shows the URL that remote clients will use to connect to this server. This is just for reference. Verify that this address will resolve and be publicly reachable from remote networks. This URL can be configured in Config > Network > Hostname.
If Server Enabled is checked, the OpenVPN server will run and accept connections from configured Remote Clients. If unchecked the OpenVPN server will not run and not server services will be provided.
Address Space defines an IP network/space for the VPN to use internally. The Address Spacemust be unique and separate from all existing networks and other address spaces on other OpenVPNs. A default will be chosen that does not conflict with the existing configuration.
NAT OpenVPN Traffic will NAT all traffic from remote networks to local networks to a local address. This helps solve routing and host-based firewall issues. The default and recommended value is enabled.
Username/Password Authentication can be enabled to activate two factor authentication, requiring clients to also provide a username and password when connecting.
Add MFA client configuration can be enabled to activate multi-factor authentication using a TOTP app. This feature uses the Local Directory users and requires each user to be configured with multi-factor authentication and paired with a TOTP app.
Authentication Method is used to select the authentication method for clients when Username/Password authentication is enabled.
Remote Clients
The Remote Clients sub-tab configures all the Remote Clients that can connect to this OpenVPN server. A Remote Client is any entity that connects to this OpenVPN server as a client. This includes both remote desktops, laptops, devices, road warriors, etc. This also includes remote OpenVPNs and remote Untangle networks.
Initially there are no clients that are allowed to connect and an unique entry must be created for each remote client you wish to allow to connect to this server.
To add a new Remote Client click on the Add and provide the following information:
- Enabled - If checked, this client is enabled. If unchecked, this client is disabled and can not connect.
- Client Name - A unique name for the client. (alphanumerics only)
- Group - The group for this client. More information below.
- Type - The type of this client. Individual Client for a single host like a remote desktop or laptop. Network for an entire remote network that the server should also be able to reach.
- Remote Networks - The remote network in CIDR notation if this remote client is of type Network. For example: 192.168.1.0/24 means that the 192.168.1.* network lives behind the remote client and should be reachable from the server. If there are multiple networks reachable through this remote client, a comma separated list of CIDR networks can be used. These networks are automatically exported such that hosts on the main network and other remote clients can reach these networks.
After configuring this information save the new Remote Client by clicking OK then Apply. After saving settings, click on the Download Client button in the Remote Clients table on the row for the new client.This will provide links to download the configuration profile for the configured client.
- Click here to download this client's configuration zip file for other OSs (Apple/Linux/etc). provides a zip file with the OpenVPN client configuration files. This file can be used to configure various OpenVPN clients for various OSs, like linux, apple, and even some phones/tables/devices.
- Click here to download this client's configuration file for remote Untangle OpenVPN clients. provides a zip file with the OpenVPN client configuration for setting up a remote OpenVPN application on Untangle to connect as a client to this server. For more information about how to install this on the remote client read the OpenVPN#Client documentation below.
- Click here to download this client's configuration onc file for Chromebook. provides a onc file that can be used to configure your Chromebook as a client to connect to the Untangle OpenVPN server. On the target device, browse to chrome://net-internals and use Import ONC file.
On the client system, you must first install the OpenVPN client. You can download the Windows client from here: https://openvpn.net/client-connect-vpn-for-windows/. Various downloadable OpenVPN clients such as Tunnelblick for macOS are available for other Operating Systems. After installing the OpenVPN client on the remote client, you can import the OpenVPN profile into the client.
Note: A client can only be connected once. If you install the same client on multiple remote devices they will kick each other off when a new one logs in. In most cases you need to setup a client for each remote device.
Groups
Groups are convenience feature to 'group' clients together and apply some settings to that entire group.By default there will be a Default Group. Each group has the following settings:
- Full Tunnel - If checked, remote clients will send ALL traffic bound to the internet through the VPN. This allows for Untangle to filter ALL internet traffic for connected clients by 'proxying' it through the VPN and then out through Untangle's internet connection. This will have no effect on remote Untangle OpenVPN clients. If unchecked, then only traffic destined to the local network are subject to filtering.
- Push DNS - If enable, OpenVPN will 'push' some DNS configuration to the remote clients when they connect. This is useful if you wish for some local names and services to properly resolve via DNS that would not publicly resolve.
- Push DNS Server - If set to OpenVPN Server then the IP of the Untangle server itself will be pushed to the remote clients and all remote clients will use Untangle for all DNS lookups. If Custom is selected then one or two DNS entries can be specified that will be used for DNS resolution.
- Push DNS Custom 1 - If Push DNS Server is set to custom, this IP will be pushed to remote clients to use for DNS resolution. It is important to export this address if that traffic should travel through the VPN tunnel. If this value is blank nothing will be pushed.
- Push DNS Custom 2 - Just like Push DNS Custom 1 except this sets the secondary DNS value. If blank, no secondary DNS will be pushed.
- Push DNS Domain - If set this domain will be pushed to remote clients to extend their domain search path during DNS resolution.
These settings will apply to all clients belonging to that group. Many sites will only have one group because all clients need the same settings. However, some clients have some Full Tunnel remote clients and some Split Tunnel remote clients. In this case, you need two groups where each client belongs to the appropriate group.
Exported Networks
Exported Networks is a list of networks that are reachable through the OpenVPN server for remote clients. Exported Networks are routes that are pushed to remote clients when they connect effectively telling remote clients to reach the specified network through the OpenVPN server.
For example, exporting 1.2.3.4/24 will result in all 1.2.3.* traffic going through the OpenVPN server.
The Exported Networks grid is pre-populated on installation with the IP/netmask of each static non-WAN interface.
- If Enabled is checked this network will be exported/pushed to connecting remote clients.
- Export Name is a name, purely used for documentation purposes.
- Network is the network, in CIDR notation.
Client
The Client tab is used to configure which remote servers this OpenVPN will connect to as a client.
Remote Servers
The Remote Servers grid lists the currently configured remote servers that OpenVPN is configured to connect to.
To configure a new server to connect to, first login to the remote server and configure a new client as described above and click on the Download Client as described above in the OpenVPN#Remote_Clients section. After you have downloaded the distribution zip file return to this OpenVPN and click on the Browse button below the Remote Servers grid. Select the zip file downloaded from the OpenVPN server and then press OK. Next press the Submit button to upload the zip file to OpenVPN which will add a new entry into the Remote Servers grid based on the configuration in the submitted zip file.
If the remote server requires Username/Password authentication, you will have to edit the configuration, enabled the Username/Password authentication checkbox, and enter the username and password to be used when establishing the connection.
Once connected to a remote server, you will be able to reach their exported networks. They will also be able to reach the networks on this server specified as the Remote Network in the OpenVPN#Remote_Clients configuration.
- Note: Site to Site connections are not full-tunnel even if selected in the Group for the site to site. Internet traffic on the remote site will exit through its local gateway.
Advanced
The Advanced tab is provided for advanced users who have a detailed knowledge and understanding of OpenVPN, and need very specific configuration changes to address unique or unusual situations. It is entirely possible to completely break your OpenVPN configuration with a single wrong character, misplaced space, or by changing a configuration option that probably shouldn't be changed. Changes you make on this page can possibly compromise the security and proper operation of your sever, and are not officially supported.
Common Settings
Openvpn Client Setup
At the top of the Advanced page are the Protocol, Port, and Cipher options. These must be the same on both the client and server for connections to work. Since they are the options most frequently modified, they can be easily configured here and will apply to both the client and server.
The Client to Client Allowed checkbox is used to enable or disable traffic passing between OpenVPN clients. When enable, all clients will have full network access to each other when connected. If disabled, traffic will not be allowed to flow between connected clients.
Server Configuration and Client Configuration
If you require changes to other low level parameters, the Server Configuration and Client Configuration grids allow you to effectively have total control of the OpenVPN configuration file that is generated. Both grids work the same way, with each configuration applied to the corresponding server or client openvpn.conf file respectively.
Both lists contain config items comprised of a Option Name and Option Value pair. By default, all items in both configuration grids are read only. The lists represent the default configuration settings used for the server and client configuration files. The default items cannot be modified or deleted, they can only be excluded. When you exclude an item, it is effectively removed from the resulting configuration file. To change one of the default items, simply add a new item with the same Option Name, and input the Option Value that you want to be used. This will effectively override the default. The same method can also be used to add configuration items that are not included in the default list.
Exclude Default Configuration Item
- This example shows how to disable the comp-lzo option in the server configuration file to turn off compression:
Modify Default Configuration Item
- This example shows how to change the default keepalive setting in the server configuration file:
Add New Configuration Item
- This example shows how to add a socks-proxy setting to the client configuration file:
Reports
The Reports tab provides a view of all reports and events for all connections handled by OpenVPN.
Reports
This applications reports can be accessed via the Reports tab at the top or the Reports tab within the settings. All pre-defined reports will be listed along with any custom reports that have been created.
Reports can be searched and further defined using the time selectors and the Conditions window at the bottom of the page. The data used in the report can be obtained on the Current Data window on the right.
Pre-defined report queries:
| Report Entry | Description |
|---|---|
| OpenVPN Summary | A summary of OpenVPN actions. |
| OpenVPN Bandwidth Usage | The approximate amount of data transfered over openvpn connections. |
| OpenVPN Events | The amount of login and logout events over time. |
| OpenVPN Sessions | The amount of openvpn sessions over time. |
| Top Clients (by usage) | The number of bytes transferred grouped by remote client. |
| Connection Events | OpenVPN client connection events. |
| Statistic Events | Shows all OpenVPN connection traffic statistics events. |
The tables queried to render these reports:
- [[Database_Schema#openvpn_stats|openvpn_stats]
Related Topics
OpenVPN FAQs
What operating systems are supported?
OpenVPN supports most operating system.
Microsoft Windows
You can download the Windows client from here: https://openvpn.net/client-connect-vpn-for-windows/. After installing the OpenVPN client, you can import the OpenVPN profile into the client.
Apple Mac
For Macs, we suggest http://code.google.com/p/tunnelblick tunnelblick.
- Download and install an OpenVPN client for MacOSX
- Login to the Untangle Server, download the client config file zip and extract the files from the zip file.
- Place it in the ~/Library/Application Support/Tunnelblick/Configurations folder on the Mac.
- Run Tunnelblick by double-clicking its icon in the Applications folder.
Linux
For all other operating systems Untangle distributes a .zip with configuration and certificate files - these can be used with any OpenVPN-compatible VPN software on any operating system.
Chrome OS
Steps to install OpenVPN on Chrome OS devices:
Can I use it with my phone or tablet?
For smartphones, you'll need to install and run a VPN client that supports OpenVPN.
iOS based iPhones and iPads
Open Vpn Client Ubuntu
For iPhones, we suggest OpenVPN Connect available on iTunes https://itunes.apple.com/us/app/openvpn-connect/id590379981?mt=8
- Install OpenVPN Connect app on your iPhone or iPad.
- Login to the Untangle Server, download the client config file by selecting 'client's configuration zip for other OSs'.
- Unzip the config file.
- Open iTunes and select the .ovpn, .crt, and .key files from the config zip to add to the app on your iPhone or iPad.
Android Based Phones
OpenVPN for Android 4.0+ is available for connecting to Untangle OpenVPN. Detailed instructions from our forum contributor WebFool. http://forums.untangle.com/openvpn/30472-openvpn-android-4-0-a.html
- Download/Install Openvpn for Android on your android unit.
- Then download the Openvpn Configuration files from the Untangle Unit.
- Unzip them and copy them to the Phone/SDcard.
- Now Open 'Openvpn for Android'
- Click 'All your precious VPNs'
- In the top right corner Click on the folder.
- Browse to the folder where you have the OpenVPN .Conf file. Click on the file and hit Select
- Then in the top right corner hit the little Floppy disc Icon to save the import.
- Now you should see 'imported profile' click on it to connect to the tunnel.
With OpenVPN, can I force all network traffic through the VPN tunnel?
Yes, you can run 'Full Tunnel' which forces all internet-bound traffic to go through the VPN and out the Untangle on the remote end (and is subject to all Untangle filtering). If running as a 'Split Tunnel' where Full Tunnell is not checked only traffic to exported networks only will go through the VPN.
Can I still use OpenVPN if my Untangle does not have a public IP?
Sometimes Untangle is installed behind another router (typically as a bridge). You can still run OpenVPN, however you will need to make some additional changes so remote clients can connect to the server:
- Port forward UDP port 1194 from your router to the Untangle server. This will allow remote clients to connect to Untangle even though it doesn't have a public IP.
- Configure your public address in Config > Network > Hostname. This is the address in the distributed clients that remote clients and networks will attempt to connect to.
Can I use OpenVPN on both of my WAN connections?
Yes. The client chooses which WAN to connect to; the server will answer via the same WAN the client connected on. The client chooses based on your configuration of Public Address. If the Public Address fails it will then try the IPs of the WANs manually as configured in the conf file.
Is there a way to setup a password for the OpenVPN users?
Openvpn Client Ios
Yes, if you right click on the OpenVPN icon on the client's PC there is an option for a password - please note this password is only used when launching the client.
OpenVPN connects, however I can not access anything. Why is this?
Many things could cause this issue. First verify that the hosts that you are trying to reach are exported in Exported Networks. After connecting OpenVPN, try to ping Untangle's LAN IP address (if exported), then try to bring up the UI by entering the IP in a browser. If these work your tunnel is up and operational. If you can't reach a Windows machine, verify Windows Firewall is disabled on the target machine as it will block access from non-local subnets by default. If the target machine runs another OS, verify it is either using Untangle as a gateway or the machine its using as a gateway has a static route sending the VPN Address Pool to the Untangle.
How can I restrict access to certain OpenVPN users?
By default, openvpn users can connect to any machine that the Untangle can connect to. However, routes are pushed to all the 'Exported' network automatically. Beware, nothing prevents adding remote users that have administrator access to their machines to add routes manually.
If restricting access to OpenVPN users is a concern, Firewall rules or Forward Filter Rules can be used. In the Firewall, the easiest way is to create a block rule blocking traffic when Source InterfaceOpenVPN. Above that rule create rules to allow traffic when Username is the openvpn user you want to allow to the desired locations. In this scenario openvpn traffic will be blocked into your network except for explicitly allowed traffic.
Using rules you can limit access to certain resources to only the desired remote users.
Can I create site-to-site tunnels with non-Untangle devices?
When using OpenVPN for site-to-site tunnels Untangle only supports using other Untangle boxes as endpoints. Some users have had success with DD-WRT and Tomato, but this is not supported by Untangle. If you need to connect a VPN tunnel to a non-Untangle device, we recommend using IPsec VPN.
I'm using site-to-site and my software clients can only talk to the main server. Why?
If you have both software clients on the road and site-to-site tunnels, the software clients will only be able to see your main site by default. To allow them to transit the tunnel(s) to other sites, simply add the VPN Address Pool to the Exported Hosts and Networks. After this is done, software clients will be able to reach all exported sites.
Openvpn Client Software
How can I allow software clients to resolve DNS over the tunnel?
To allow DNS resolution for remote clients you'll need to modify some OpenVPN settings - if Untangle is doing DNS resolution on your network, simply check Push DNS in OpenVPN Settings > Server > Groups > Group Name for any groups you want to push DNS settings to. Configure the DNS settings you would like pushed to the remote clients. You may need to use the FQDN when accessing resources across the tunnel.
How do I auto-start OpenVPN when my computer boots?
This only applies to Windows XP Pro, Vista, & Windows 7 to auto-start OpenVPN on boot:First, Navigate to C:Program FilesOpenVPNconfig. This directory will have sitename.conf, sitename.ovpn and subdirectory untangle-vpn. In this directory, identify the .ovpn file that corresponds to your site's name.
Modify OpenVPN
- Go to START > Control Panel > Administrative Tools > Services
- Right click on OpenVPN and select Properties
- Change Startup Type to Automatic
- Click OK
- Close the Services window
- Close the Administrative Tools window
- Close Control Panel
Modify Registry
- Go to Start > Run > Regedit
- Follow path down to: HKLMSOFTWAREMicrosoftWindowsCurrentVersionRun
- Locate the entry for 'openvpn-gui'
- The command reference should say: C:Program FilesOpenVPNbinopenvpn-gui.exe
- MODIFY IT TO: C:Program FilesOpenVPNbinopenvpn-gui.exe --connect sitename.ovpn. Where sitename is customized for your specific site.
- Modify the following registry value to 1: HKEY_LOCAL_MACHINESOFTWAREOpenVPN-GUIallow_service
- Exit RegEdit
When the machine restarts, the user will automatically be connected with the VPN client.
Clients are getting disconnected after 60 seconds. Why?
Did you share the same client config between multiple machines. If both are running they will conflict. When the second one connects the first is disconnected. After 60 seconds the first will reconnect and disconnect the second. This repeats endlessly. Do not share the same client config with multiple machines.
I'm setting up a new client and can't connect. Why?
Make sure that the IP that the client is connecting to is the public IP of the server, or that the traffic to that IP on port 1194 is being forwarded to your server. Also make sure you are testing from the outside. By default the Access Rules block OpenVPN clients from connecting to a server from one of its own LANs. This is to prevent clients from losing connectivity while on the local network because of a routing loop.
How do load a 9.4.x (server) remote network client zip on a 10.x Untangle (client)
9.4.2 site-to-site client zip will load on 10.x without modifications. 10.x has built-in converters to load 9.4 configuration zip files.
How do load a 10.0 and later (server) remote network client zip on a 9.4.x Untangle (client)
The directory structure of the client config zip has changed in 10.0. This means 9.4 Untangle instances will not load 10.0 and later config zip files correctly. The workaround is to modify the 10.0+ zip file to the 9.4 directory structure.
Modify OpenVPN config zip file for use on 9.4 instances
- Download client config zip from 10.0 OpenVPN server.
- Unzip the config zip.
- The directory structure is
- openvpn-<name of untangle>-config
- untangle-vpn
- untangle-<random number>.conf
- untangle-<random number>.ovpn
- key <--- rename this directory to untangle-vpn
- untangle-<random number>-<name of untangle>.crt
- untangle-<random number>-<name of untangle>.key
- untangle-<random number>-<name of untangle>-ca.crt
- untangle-vpn
- openvpn-<name of untangle>-config
- Modify untangle-<random number>.conf and untangle-<random number>.ovpn files
- Change the following lines:
- cert key/untangle-4855-FortWayne.crt
- key key/untangle-4855-FortWayne.key
- ca key/untangle-4855-FortWayne-ca.crt
- To:
- cert untangle-vpn/untangle-4855-FortWayne.crt
- key untangle-vpn/untangle-4855-FortWayne.key
- ca untangle-vpn/untangle-4855-FortWayne-ca.crt
- Change the following lines:
- Rezip the directory structure from the top untangle-vpn folder
- Import this new remote openVPN client config file to the 9.4 Untangle in VPN client mode.